
Picture this. An email pings your inbox. It’s from the Managing Director or Group CEO. Short, urgent, and commanding: “Approve this transfer before noon.” For many Nigerian professionals, that instruction carries immediate weight. In our workplaces, where hierarchy is deeply respected, the instinct to act fast often overshadows the instinct to pause. That is why Business Email Compromise (BEC) is thriving.
BEC doesn’t depend on sophisticated malware. It thrives on psychology. Attackers know that in many Nigerian companies, leadership’s voice is rarely questioned. They exploit that cultural reflex – turning trust in authority into a weapon.
Anatomy of a fake CEO scam
BEC is sometimes called “CEO fraud,” and the label isn’t far from the truth. Attackers spoof an executive’s email or compromise the real account using stolen credentials. Then they send simple, believable messages – often stripped of attachments or logos.
Common tricks Nigerian businesses face include:
The genius of BEC lies in its simplicity. These emails don’t look suspicious. They blend seamlessly into daily business communication.
BEC works not because our professionals lack training, but because attackers exploit how businesses operate here.
Ask yourself: if your CFO sends an email at 7:30 a.m. demanding a transfer before 9, would you question it? Or would you process it immediately, afraid of being seen as uncooperative? That’s where BEC lands its strike.
Globally, BEC is one of the most expensive cybercrimes. The FBI’s Internet Crime Complaint Center recorded over 2.9 billion dollars in losses in 2023. While Nigerian-specific data is harder to come by, the Central Bank of Nigeria and NDIC have repeatedly warned about increasing fraud incidents targeting banks, fintech’s, and even government agencies.
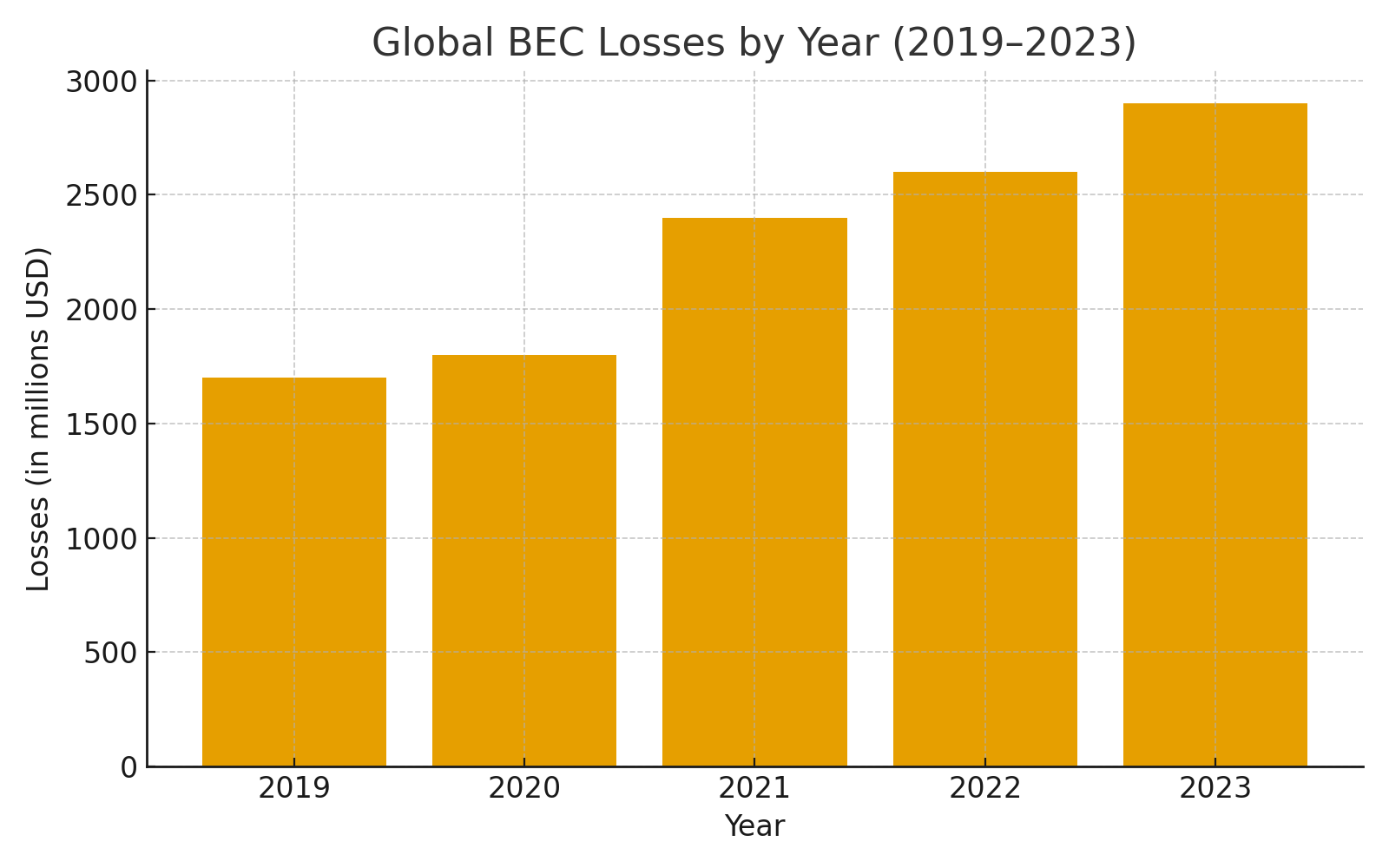
Figure 1: Global BEC Losses by Year (2019–2023)
Two truths stand out:
The message is clear: whether you’re a multinational or a microbank, BEC is a real and present threat.
Look out for these red flags in emails that appear to come from leadership:
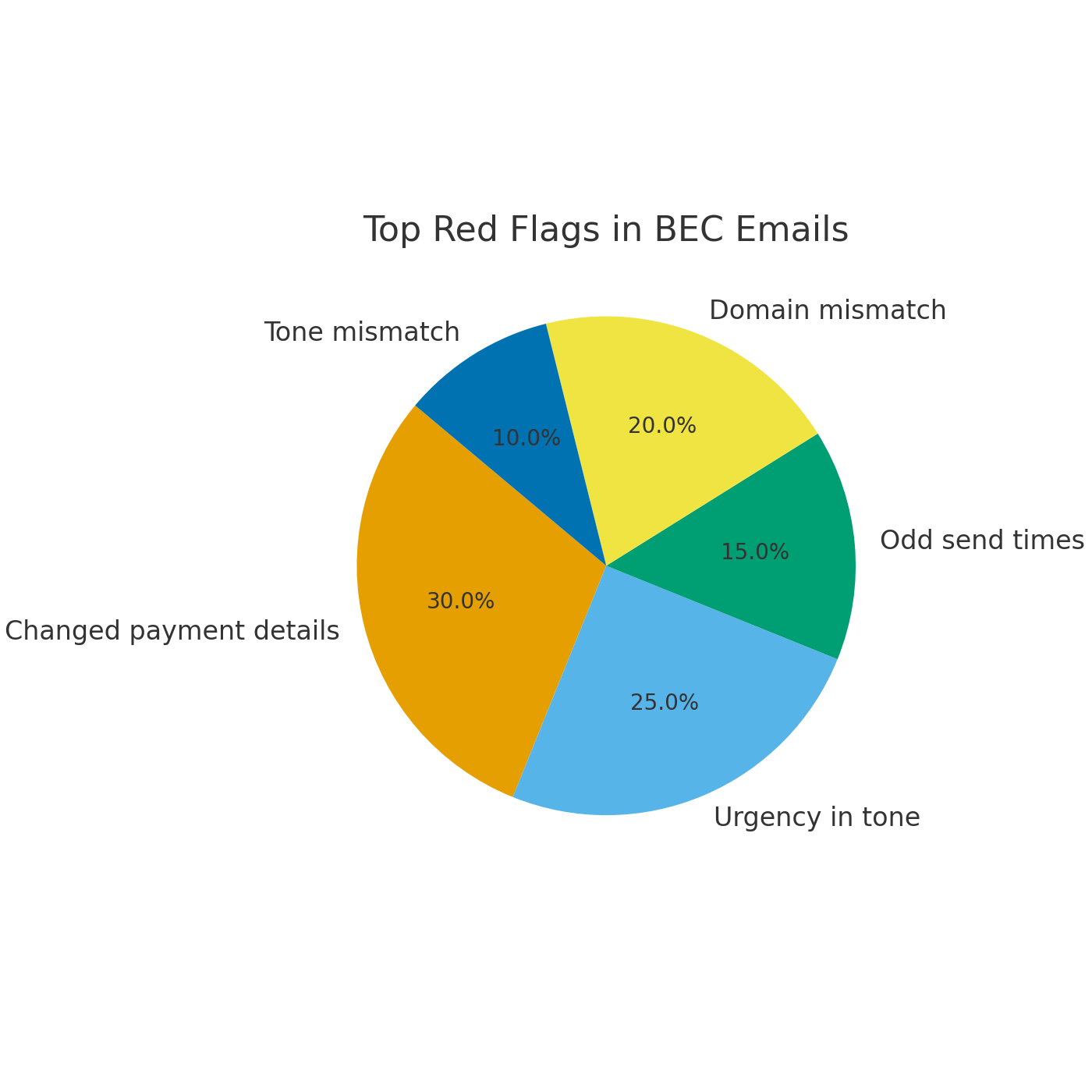
Figure 2: Top Red Flags in BEC Emails Reported by Enterprises
When two or more of these signs appear together, staff should be empowered to stop and verify.
Tools are vital, but culture is everything. Nigerian organisations should adopt:
But even the best tools won’t work without cultural change. Staff must feel safe asking, “Oga, are you sure about this request?” Leaders should openly encourage verification, removing fear of insubordination. That mindset shift is the ultimate defense.
Think of how Nigerian travelers respond when the airline staff calls “final boarding.” Passengers rush, sometimes leaving luggage behind. Urgency bypasses rational thought. That’s exactly why attackers use it. Recognizing urgency as a deliberate tactic helps teams slow down before making mistakes.
Tomorrow’s BEC will be more convincing. Attackers are already cloning voices of CEOs using AI tools. Imagine receiving a call in your MD’s voice confirming a transfer. Or attending a Zoom meeting where a deepfake executive asks for an urgent favor.
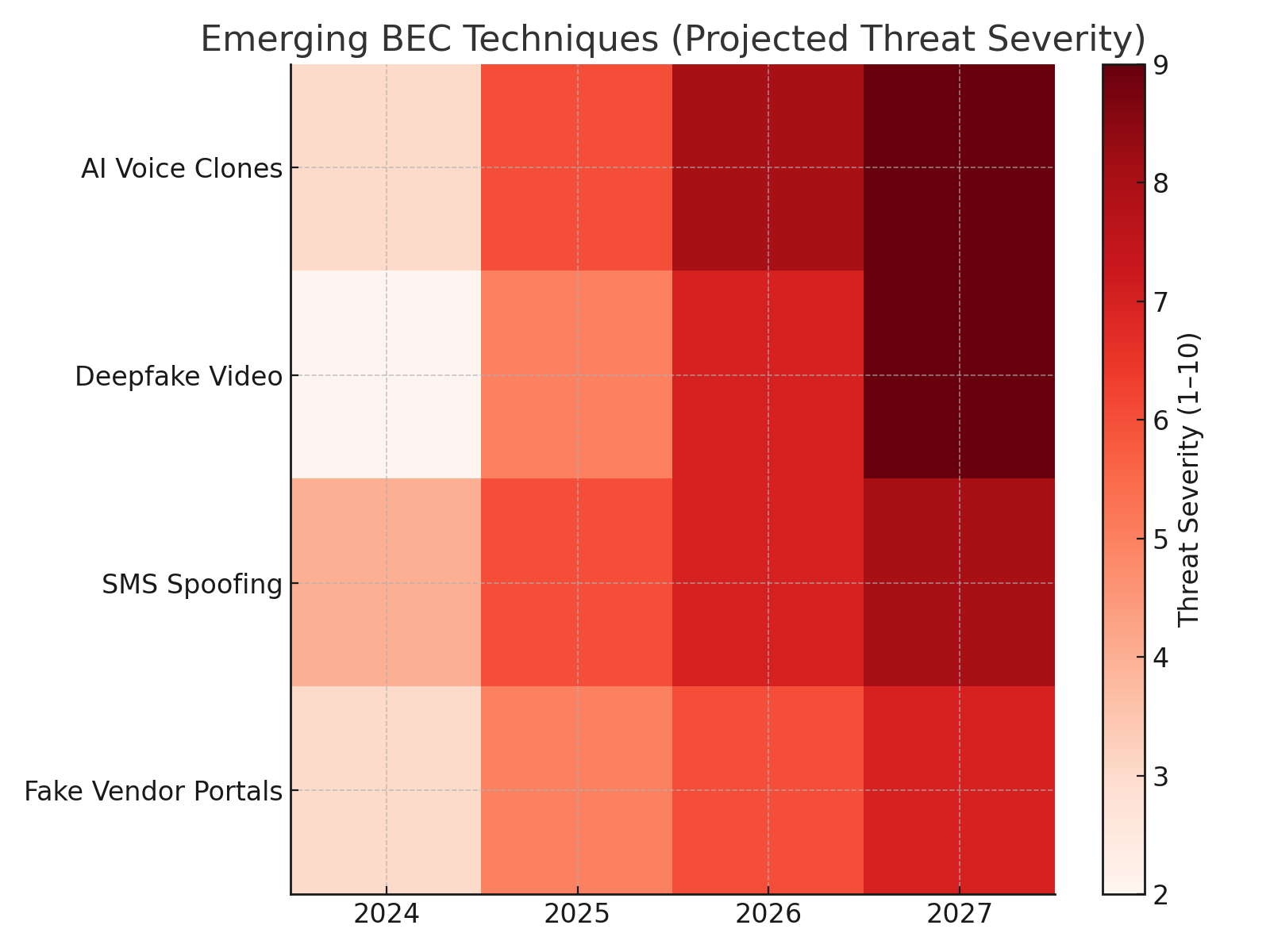
Figure 3: Emerging BEC Techniques: AI Voice, Deepfakes, SMS Spoofing
Nigeria, with its growing fintech and digital banking sector, will be a prime target. The response must be proactive – zero-trust verification, multi-channel approvals, and training staff to expect manipulation.
Every department has a role:
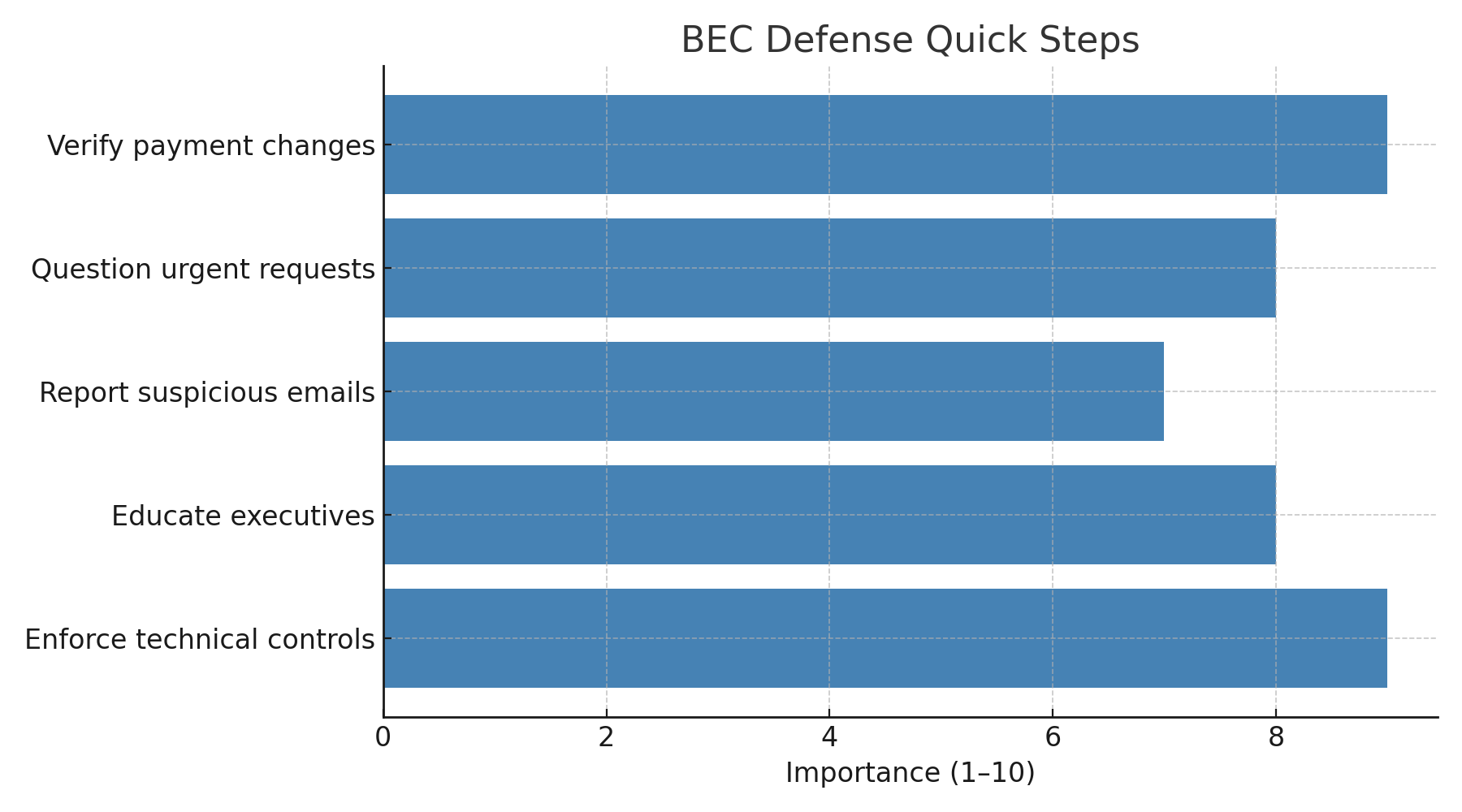
Figure 4: BEC Defense Quick Steps
BEC thrives where respect for hierarchy and urgency collide. In Nigeria, where both carry heavy weight in the workplace, attackers find fertile ground. Breaking their grip requires not only stronger tools but stronger culture.
The smartest defense for Nigerian businesses is to normalize verification. Empower employees to pause, confirm, and challenge – even if the request comes “from the top.”
Because at the end of the day, protecting the company is everyone’s job.