
Remote work is no longer a temporary fix. For many organizations, it’s the norm, and that shift has brought a new security reality: endpoints are everywhere. Laptops, mobile phones, IoT devices, and even smart printers are now potential gateways for attackers. One overlooked configuration or outdated patch could be all it takes for a breach to happen. That’s why endpoint management is no longer a “back-office IT chore” — it’s a front-line defense.
Attackers aren’t breaking in through fortified firewalls as often as before. They’re slipping in through endpoints left unpatched, unmanaged, or misconfigured. A single unsecured laptop connected to public Wi-Fi can expose your corporate network to malware or ransomware. In fact, recent security reports have shown that compromised endpoints are responsible for a significant percentage of data breaches.
Think of each endpoint as an unlocked side door to your network. It doesn’t matter how strong your main entrance is if those side doors stay open.
Managing devices individually is like trying to guard a castle with a dozen drawbridges and only one guard per bridge. Centralized endpoint management platforms such as Microsoft Intune, VMware Workspace ONE, or ManageEngine Endpoint Central allow IT teams to oversee every device from one dashboard. This means quicker patch deployments, faster incident response, and a clearer view of vulnerabilities.
When all devices are under a single umbrella of policy and visibility, you avoid the chaos of fragmented security controls.
An outdated OS or unpatched application is an open invitation for attackers. Cybercriminals are quick to exploit known vulnerabilities, often within hours of a patch being released. Automating your patch management process ensures no device slips through the cracks. Tools like Automox or Ivanti Neurons help schedule and enforce updates without waiting for users to hit “remind me later.”
The key here is consistency. If even one device is missed, it’s enough to compromise the network.
Endpoints should never be treated as personal playgrounds. Use role-based access control so that employees only access the resources necessary for their jobs. Combine this with multifactor authentication (MFA) for all endpoint logins. Even if credentials are stolen, MFA adds an extra barrier that’s hard for attackers to bypass.
This is especially critical in remote work scenarios where devices may connect from multiple networks — some of them far from secure.
Endpoint detection and response (EDR) tools like CrowdStrike Falcon, SentinelOne, or Microsoft Defender for Endpoint give IT teams real-time visibility into suspicious activity. Instead of waiting for a breach to make the news, you can detect unusual patterns, isolate affected devices, and prevent spread before serious damage occurs.
Think of this as having a security camera system that not only records but also alerts you when someone’s picking the lock.
Mobile devices are now full-fledged workstations. They hold company emails, documents, and apps that connect directly to the corporate network. Mobile Device Management (MDM) tools are essential for enforcing encryption, remotely wiping lost devices, and controlling app installations.
A lost phone without security controls isn’t just an inconvenience — it’s a breach waiting to happen.
An inactive device connected to your network is like a forgotten key still working on the office door. Schedule regular device audits to identify and remove outdated or unused endpoints from your environment. Every inactive device you retire reduces your attack surface.
These audits often reveal surprising findings — from old intern laptops to forgotten IoT gadgets still online.
Your IT team’s efforts won’t matter if employees bypass controls or ignore security warnings. Regular, concise training sessions on phishing awareness, safe network practices, and endpoint security hygiene keep staff alert.
Training shouldn’t be a dull slideshow — mix in real examples, quick quizzes, and even simulated phishing attempts to keep engagement high.
Too many restrictions can frustrate employees and lead them to find workarounds. The goal is to design policies that keep endpoints secure without disrupting daily operations. Involve department heads in policy discussions so you understand workflow needs before enforcing changes.
Sometimes, a small tweak in access rules or application controls can improve compliance without sacrificing security.
With AI tools integrated into everyday workflows, endpoints often store sensitive training data or connect to AI-driven applications. This makes them high-value targets for attackers seeking to poison datasets or steal proprietary models. AI security posture management should extend to endpoint monitoring, ensuring these devices remain uncompromised.
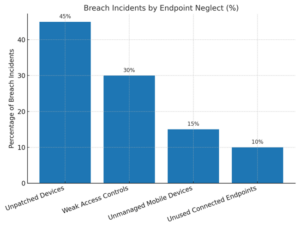
Comparing breach incidents caused by unpatched devices, weak access controls, unmanaged mobile devices, and unused endpoints still connected.
The data makes one thing clear — poor endpoint management isn’t a minor gap, it’s a primary cause of breaches.
Endpoint management is no longer optional maintenance work for IT. It’s a critical security practice that directly impacts whether your organization stays safe or becomes the next breach headline. Centralized control, consistent updates, strict access policies, active monitoring, and informed users form the backbone of strong endpoint security.
Your IT team’s attention to these practices will decide whether your endpoints are fortified gates or wide-open entry points.