
The last few years have felt like a long sprint for security teams in Nigerian financial institutions. You close one gap and another opens somewhere else. You update a policy and, before you finish the rollout, attackers shift tactics again. Progress is real. The wins are real. Your teams have tightened identity controls, modernized monitoring tools, cleaned up risky legacy systems, and reduced the attack surface in more than a few critical areas.
Still, every improvement seems to invite a fresh challenge. The volume of threat activity linked to financial services keeps rising. Attackers are hunting for smaller cracks. They use more automation. They shift between social engineering on Monday and credential stuffing by Wednesday. You feel the pace. Everyone on your team feels it. No one seems to get a breather anymore.
There is a reason for this. Money creates motivation. Financial institutions hold the highest-value data in the region, so threat groups stay locked in. Every trend report from the last two years points toward one pattern, which is the rapid evolution of financially motivated attacks targeting Nigerian institutions. The escalation is steady. You see it in your SOC metrics. You see it in audit findings. You see it in staff phishing tests when employees fall for messages that look almost identical to internal memos.
The encouraging part is the direction many financial institutions are heading. Zero trust adoption is growing. MFA fatigue attacks are taken seriously now instead of treated as fringe experiments. Network segmentation is no longer optional. There is forward progress. But progress without speed feels like standing still, especially when adversaries move faster with fewer constraints.
You do not control the speed of attackers. You control the speed of your response, the strength of your architecture, and the clarity of your communication with customers. That balance shapes everything.
Nigerian financial institutions face sustained pressure from groups focused on financial gain. These groups run phishing campaigns that mimic internal system prompts. They automate reconnaissance on exposed infrastructure. They test thousands of stolen credentials from unrelated breaches, hoping a handful match an employee account. They try SIM swap tactics. They track executives on social media. Some even monitor developer forums and cloud repositories hoping to find forgotten tokens.
These tactics are not theoretical. Your teams already deal with them. The numbers tell part of the story. Reports across the industry show consistent growth in breach attempts targeting financial institutions from 2021 through 2024. The chart below summarizes that climb using simplified data that reflects the trend acknowledged by multiple Nigerian security teams.
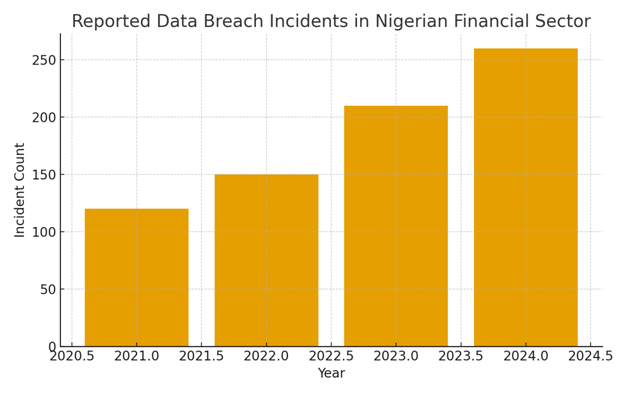
The rise in attempts is equally important. You already know attempted attacks do not always translate into breaches, but the increase shows aggressive probing across digital channels. That creates a different kind of pressure. It means constant alert noise, more telemetry to review, and more oversight on third-party configurations. The trend looks like this:
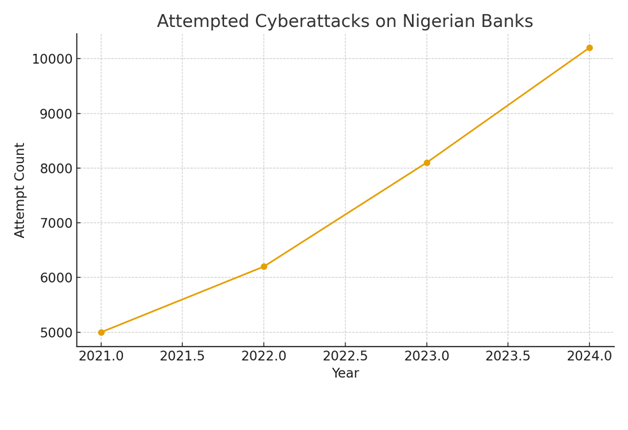
If you oversee any SOC or engineering function, this pattern looks familiar. You are handling more signals than you did four years ago. You are validating more anomalies. You are watching threat actors test authentication flows at odd hours. Attackers are not only multiplying their attempts. They refine them in increments that catch organisations off guard.
Nigerian financial institutions have invested in newer security tools. Identity governance programs have matured. Encryption policies are no longer negotiable. Data classification is no longer a theoretical compliance requirement. You would expect a sharper decline in breaches.
Yet breaches still occur.
Not because teams lack skill. Not because institutions are careless. The reason is simpler. Attackers adapt more quickly than financial institutions can restructure. You deal with legacy infrastructure, regulatory expectations, staffing limitations during budget cycles, vendor dependencies, system modernization projects running in parallel, and pressure to push digital banking features without slowing the roadmap.
Attackers do not carry those constraints. They adjust in an afternoon. Your teams need weeks or months. That lag creates openings.
Another factor is customer behavior. A significant portion of compromises stem from customers who fall for social engineering tricks. Fraud rings design messages that match alerts from actual banking apps. They mimic the tone of call centre agents. They build fraudulent onboarding flows. They impersonate a bank’s security department through cloned WhatsApp lines.
You recognize the issue. You have warned customers in newsletters, app notifications, and SMS reminders. Still, some individuals trust the wrong caller on a stressful day. That single decision feeds part of the threat ecosystem.
Different banking segments face different risks. Retail banking sees the highest customer-level threats. Corporate banking deals with targeted credential theft and vendor compromise. Digital banking teams face the fastest attack cycles. To underscore this variation, here is a simple heatmap capturing the exposure pattern across confidentiality, integrity, and availability:
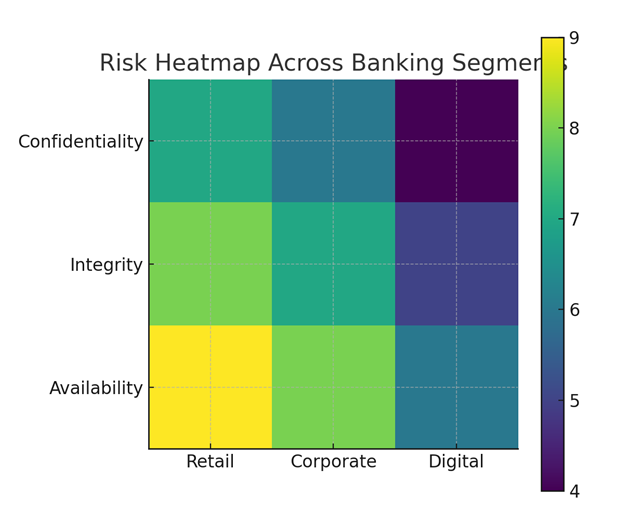
The point is clear. Every segment carries risk in a different shape. The response needs the same precision.
One of the most overlooked levers in financial security today is customer awareness. You already train staff. You already have policies for internal behavior. Customers, however, form one of the most unpredictable risk surfaces for Nigerian financial institutions.
A customer may click a malicious link during a busy commute. Another may share sensitive information while trying to resolve a transaction dispute. Fraudsters actively target emotional triggers. They rush people. They manufacture urgency. They imitate internal language patterns from real employee emails.
You have warned customers before, and you will warn them again. But traditional reminders lack power when used alone. Customers need contextual education. They need guidance through examples. They need material that reflects local tactics instead of generic global templates. They need short, frequent reminders instead of rare broadcast messages. Most importantly, they need support that acknowledges pressure. If a customer feels embarrassed after falling for an attempt, they hesitate to report. That delay benefits attackers.
Your bank holds the responsibility to lower that emotional barrier.
Zero trust has been viewed as a technical architecture shift. You segment the network. You validate identity. You enforce continuous authentication. You verify device health. You monitor access patterns. All of this creates a stronger internal posture.
What often gets missed is the cultural shift around it. Zero trust helps your teams slow the spread of attacker movement. The model helps isolate abnormal behavior that would otherwise slip into the background noise of traditional monitoring. The model also clarifies responsibilities. Everyone becomes accountable for their own access decisions.
Zero trust helps because it removes assumptions. Attackers depend on assumptions. If no one assumes trust, attackers lose the advantage.
Many Nigerian financial institutions have begun adopting zero trust principles. A few are far along. Others are in early discovery. The pace differs. The direction does not. The demand for stronger identity controls continues to rise through regulatory expectations and internal risk assessments.
Financial institutions operate in an environment where customers expect convenience. Digital onboarding needs to be fast. Transactions need to go through in seconds. Fraud detection needs to run quietly without delaying payments. Every part of the system must be smooth. This pressure pushes teams to innovate quickly.
But the same speed that improves customer experience increases exposure when controls lag behind. Attackers exploit misconfigurations that appear when systems are deployed faster than they are secured. Modern architectures rely on distributed components. Distributed components create more points of entry. More points of entry create more responsibility for teams already carrying heavy workloads.
This is why acceleration in security matters. Not rushed acceleration. Informed acceleration.
Security teams know the areas where modernization needs stronger discipline, including API access governance, cloud permission hygiene, legacy system decommissioning, endpoint controls for remote staff, consistent MFA enforcement, secure CI pipelines, and vendor risk validation.
Attackers often find gaps in one of those domains. When those gaps align with a period of high operational stress, a breach becomes more likely.
Progress is measurable. Nigerian financial institutions are no longer where they were in 2018 or 2020. The depth of internal expertise has increased. Modern security tooling is more common. The number of incident response teams with cloud fluency continues to grow. Encryption standards are higher. Access reviews are more structured.
The challenge is the gap between progress and pace.
Closing that gap depends on three shifts.
First, stronger customer education. Customers play an unintentional role in fueling intrusions. Giving them structured, consistent guidance reduces a large class of attacks.
Second, a full embrace of zero trust. Not the partial adoption seen in some institutions. A complete shift with identity at the centre. That shift reduces the impact of compromised credentials, which account for a large percentage of unauthorized access attempts.
Third, better visibility. Asset discovery affects every part of a security program. If you do not know what is running, you cannot protect it. Shadow systems, forgotten dev environments, unmanaged scripts, and inconsistent patch cycles remain common sources of incidents across the sector.
To support these ideas, the visual below summarizes a baseline security checklist tailored to Nigerian financial institutions:
Security teams in Nigerian financial institutions juggle operational demands that rarely slow down. You manage compliance reviews. You respond to auditors. You support product teams under pressure. You monitor logs late at night. You handle escalations when a customer reports suspicious activity. You revise policies. You test backups. You meet regulators. You train staff. You inspect cloud workloads. You monitor vendor access. You review suspicious network paths. You prepare reports for leadership.
In this environment, new threats land on top of old responsibilities. Yet every improvement builds resilience, even the small ones.
You do not need perfection. You need direction. You already have it: faster detection, stronger authentication, tighter access boundaries, consistent customer communication, and ongoing architecture modernization.
Nigerian financial institutions are progressing. Attacker activity is progressing as well. The advantage goes to whoever moves with more discipline. Your team is already on the right path.
If you sustain the improvements, speed up targeted areas, and balance innovation with controlled execution, the sector will stand stronger than ever.
When customers trust your systems, they trust your brand. When security teams feel supported, they deliver better outcomes. When attackers meet stronger defenses, they shift away.
Progress is not the absence of breaches. Progress is the reduction of avoidable risk. You have the expertise. You have the visibility. You have the roadmap. The next steps rely on deeper commitment, sharper execution, and more unified effort across technology, operations, and customer communication.
The threat is evolving fast. Your response needs steady momentum and thoughtful action. Every improvement matters. Every control adds weight. Every trained customer adds another layer of defense.
This is how Nigerian financial institutions stay ahead. This is how the sector builds resilience that lasts.
Dumeh Technologies helps public and private organizations strengthen their cybersecurity posture through managed services, compliance consulting, and AI-driven threat detection. We are committed to supporting Nigeria’s digital transformation by delivering secure, reliable, and forward-thinking solutions that safeguard what matters most – data, trust, and people.