
Digital transformation is in full swing across Nigeria. From fintech startups reshaping banking to e-commerce platforms serving millions, the digital economy is growing fast. But here’s the catch: the more connected we become, the more vulnerable our systems get. And in a country where cybercrime is evolving faster than many businesses can adapt, that’s a serious issue.
If you’re running a business in Nigeria today, cybersecurity shouldn’t be an afterthought. It needs to be at the core of your operations — as critical as power, payroll, or profit. Whether you’re a Chief Information Security Officer, part of an IT team, or a decision-maker shaping policy, the threats are real, and the time to act is now.
This article explores practical steps your organization can take to protect endpoints, detect threats early, and assess vulnerabilities before attackers do. Let’s get into it.
Nigeria’s internet penetration is rising. So is mobile usage, digital payments, and remote work. But while digital adoption accelerates, cybersecurity awareness hasn’t kept pace.
Attackers are exploiting that gap.
Phishing scams, business email compromise (BEC), ransomware attacks, and insider threats have become common. Some criminals are local. Others are operating internationally. What they all have in common is this: they’re targeting weak spots, and Nigerian businesses are often in their crosshairs.
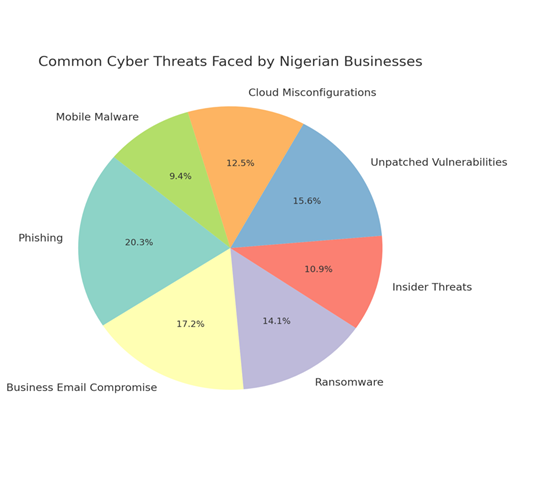
Figure 1: Common Cyber Threats Face by Nigerian Businesses
Think of endpoints as your digital front door. Laptops, smartphones, servers, ATMs, POS systems — every one of them is a potential entry point for an attacker.
So, what happens when that door is left open?
Endpoints are often exploited because they’re numerous, widely distributed, and managed inconsistently. One outdated device. One compromised app. That’s all it takes.
Without strong endpoint protection, your network is only as secure as the least secure device connected to it.
Spotting Trouble Before It Spreads: Threat Detection Done Right
By the time attackers steal your data or lock your systems, it’s too late. That’s why early detection matters.
You can’t defend what you can’t see.
Threat detection means more than just antivirus software. It requires continuous monitoring, context-aware alerts, and fast response times. Nigerian businesses often operate with lean IT teams, which makes automation and smart tools even more valuable.
What you need is visibility. Without it, attacks will happen silently. With it, you get a chance to stop them before the damage spreads.
Vulnerability Assessments: Finding the Gaps Before Others Do
Every system has weak spots. The smart move is to find yours before someone else does.
That’s where vulnerability assessments come in. These help you identify misconfigurations, unpatched software, exposed services, and policy gaps. They’re not the same as penetration tests — which simulate real-world attacks — but both have their place.
Make vulnerability assessment part of your change management and DevSecOps processes. Don’t treat it like a one-time event.
People Are the Wild Card: Train Them Well
No matter how strong your firewalls or how advanced your EDR tools are, they won’t stop an employee from clicking on a fake invoice or giving up credentials over the phone.
Security awareness training isn’t optional.
Train your staff to recognize phishing, social engineering, data handling mistakes, and insider threats. And don’t make training a once-a-year PowerPoint session. People forget.
People can be your best line of defense — but only if they understand the risk and know what to do.
Watch Out for Insider Threats (Yes, Even in Small Teams)
It’s not always external attackers. Sometimes the threat is internal.
A disgruntled staff member. A curious intern. An overworked developer who takes shortcuts. Insider threats can be accidental or deliberate. Either way, the damage can be serious.
In smaller organizations, it’s easy to trust everyone. But that trust needs to be backed by process.
Remote work isn’t going anywhere. Neither is cloud adoption. But both come with new risks.
With employees working from cafés, homes, and shared co-working spaces, the perimeter is gone. And cloud systems — while flexible and scalable — are only secure if configured properly.
The goal isn’t to block flexibility. It’s to enable it without risk.
Build a Culture, Not Just a Checklist
Security isn’t a project with a finish line. It’s a culture. And culture starts at the top.
Leadership needs to speak the language of risk. Teams need to know where to report incidents. Security shouldn’t be seen as the department of “No,” but as the team that protects innovation.
If security feels like a burden, something’s off. The best programs are practical, understandable, and aligned with business goals.
Final Checklist for Nigerian Businesses
Don’t wait for a breach to happen. Build now.
Cybersecurity isn’t a tech issue. It’s a business risk. And in Nigeria’s fast-growing digital economy, that risk is only increasing.
The good news? You don’t need a massive budget to make a difference. What you need is commitment, process, and the right tools. Start with the basics. Stay consistent. And keep learning.
Your reputation, customer trust, and long-term survival depend on it.